Day 31. Network Devices
CompTIA Network+ N10-006 Exam Topics
- 1.1 Explain the functions and applications of various network devices
Key Topics
Today’s review focuses on the network device functions, including common devices and specialty devices.
Common Network Devices
Designing, installing, administering, and troubleshooting a network requires the ability to recognize various network components and their functions. Table 31-1 lists several common network components and their functions.
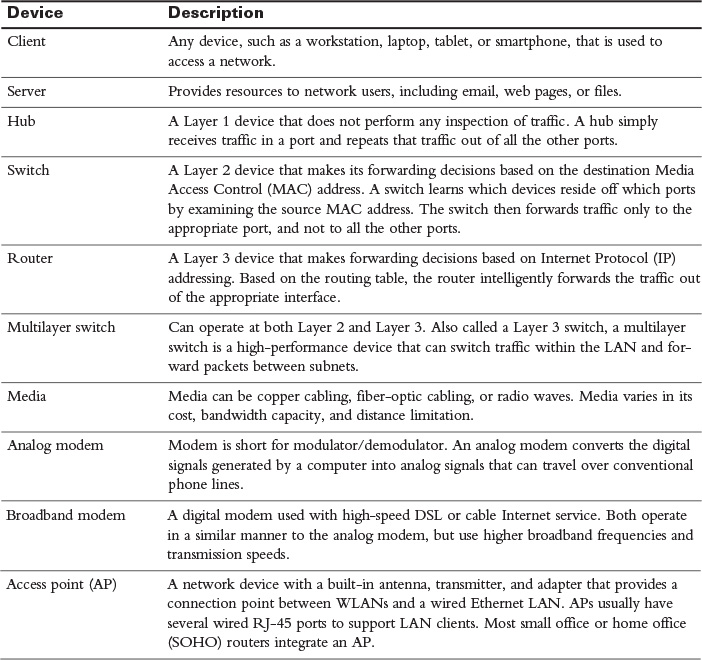
Table 31-1 Common Network Device Functions
Some of the devices listed in Table 31-1 are shown in Figure 31-1.
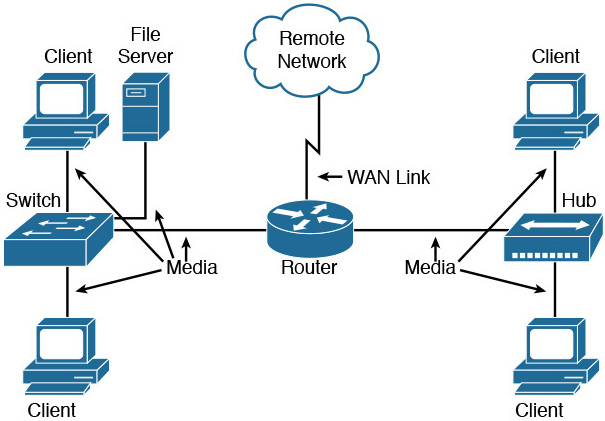
Figure 31-1 Common Network Components
Specialty Devices
Although common network devices make up the backbone of a network, many networks integrate various specialized network devices.
Firewalls
A firewall is a networking device, either hardware or software based, that controls access to your organization’s network. This controlled access is designed to protect data and resources from outside threats.
Organizations implement software firewalls through network operating systems (NOS) such as Linux/UNIX, Windows servers, and Mac OS X servers. The firewall is configured on the server to allow or block certain types of network traffic. Hardware firewalls are often dedicated network devices that can be implemented with little configuration.
A basic firewall is shown in Figure 31-2.
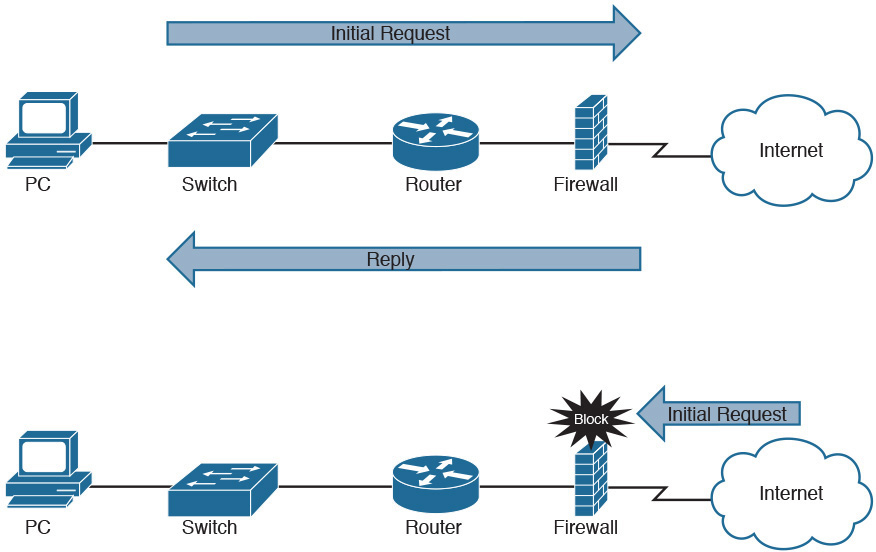
Figure 31-2 The Function of a Firewall
IDS and IPS
Both intrusion detection systems (IDS) and intrusion prevention systems (IPS) can recognize network attacks; they differ primarily in their network placement. An IDS device receives a copy of traffic to be analyzed. An IPS device is placed in line with the traffic, as shown in Figure 31-3.
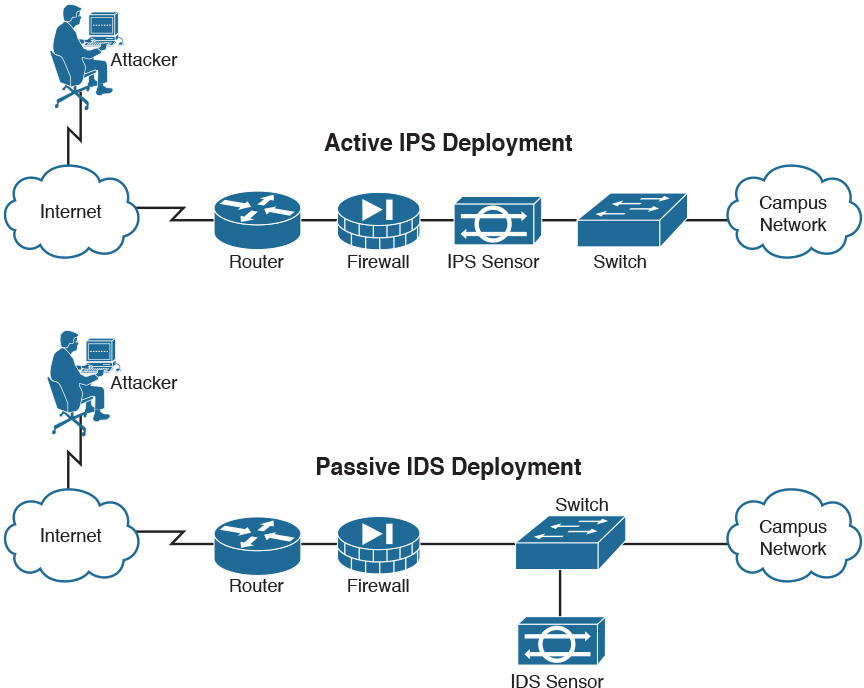
Figure 31-3 IPS and IDS Comparison
An IDS is a passive detection system. It can detect the presence of an attack, log the information, and send an alert.
Following are several variations on IDSs:
- Behavior-based IDSs look for variations in behavior so they can recognize potential threats and quickly log the information as well as send an alert.
- Signature-based IDSs evaluate attacks based on attack signatures and audit trails. This type of IDS uses an extensive database to determine the signature of the traffic.
- Network-based IDSs (NIDS) examine all network traffic to and from network systems.
- Host-based IDSs (HIDS) include applications such as spyware and virus applications that are installed on individual network systems.
An intrusion prevention system (IPS) includes the functionality of an IDS. However, an IPS is an active device that continually scans the network, looking for inappropriate activity. It can shut down any potential threats. The IPS looks for any known signatures of common attacks and automatically tries to prevent those attacks.
Proxy Server
A proxy server is a computer that provides a computer network service allowing clients to make indirect network connections to other network services. A proxy server can effectively hide the IP addresses of a trusted network because all requests going out to the Internet are sourced from the proxy server’s IP address, as shown in Figure 31-4.
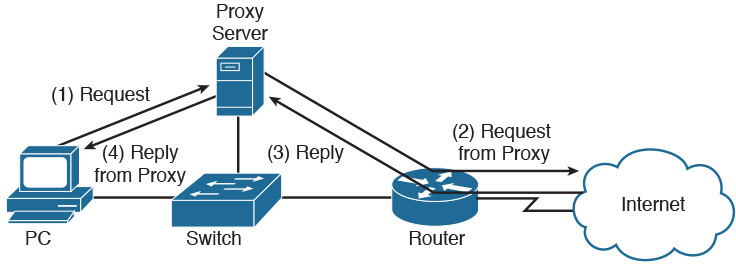
Figure 31-4 Proxy Server Operation
Reverse proxy is used when a proxy server protects another server (normally a web server) that responds to requests from users on the other side of the proxy server. Proxy servers can also conserve expensive WAN bandwidth by performing content caching. In addition, proxy servers can provide content filtering services.
Content Caching
When the user first visits a website, the proxy server will store the website for a configurable amount of time. When another user requests the website, the proxy server will check to see if the website has changed. If not, the proxy server can locally serve up the content. Proxy servers can also serve as content filters.
Content Filter
A content filter is software that usually controls what websites a user is allowed to access. An employer can block access to specific types of sites for all users, some users, or even just an individual user. The filter can be applied as software on client machines, on a proxy server on the network, at the Internet service provider (ISP), or even within the search engine itself. The latter is most commonly used on home machines or SOHO routers, and an example is Content Advisor in Internet Explorer.
Load Balancer
For companies with a large Internet presence, a single server could be overwhelmed with requests flooding in from the Internet. To alleviate the burden placed on a single server, a load balancer distributes incoming requests across mirrored servers, as shown in Figure 31-5.
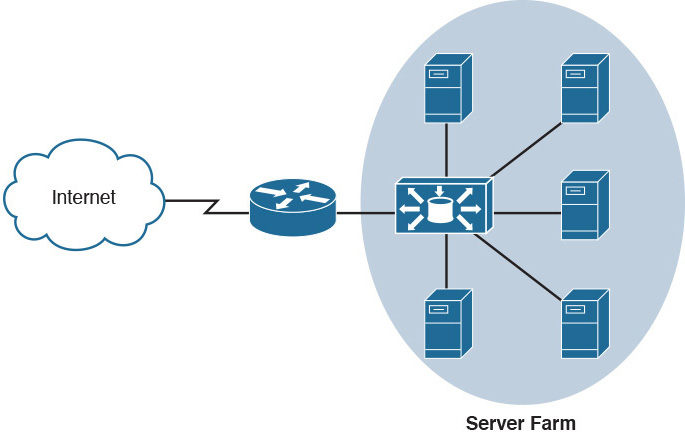
Figure 31-5 Load Balancer Scenario
Load balancers allow a server farm to scale. As demand increases, new servers can be added. Maintenance is also easier because a failed server can be replaced with little or no impact to the service level experienced by users.
Packet Shaper
Traffic shaping establishes priorities for data traveling to and from the Internet and within the network. A packet shaper essentially performs two key functions: monitoring and shaping. Monitoring includes identifying where usage is high and the time of day. After that information is obtained, administrators can customize or shape bandwidth usage for the best needs of the network.
VPN Concentrator
A virtual private network (VPN) provides a cost-effective way to create a secure connection, or tunnel, through an untrusted network such as the Internet. Although several router models can terminate a VPN circuit, a VPN concentrator can be used instead to perform the processor-intensive processes required to terminate multiple VPN tunnels. Figure 31-6 shows a sample VPN topology, with a VPN concentrator at each corporate location.
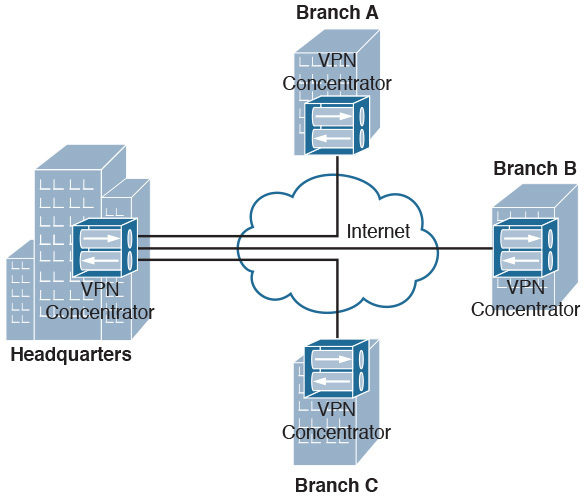
Figure 31-6 VPN Concentrator Scenario
 Video 31.1—Network Devices – Function and Application
Video 31.1—Network Devices – Function and Application
 Video 31.2—Proxy Servers
Video 31.2—Proxy Servers
 Activity: Compare Network Devices
Activity: Compare Network Devices
Study Resources
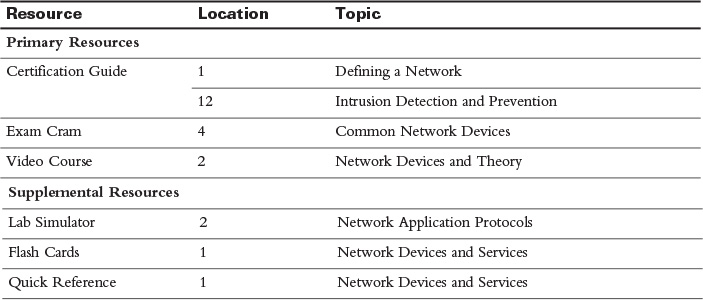
For today’s exam topics, refer to the following resources for more study.
 Check Your Understanding
Check Your Understanding