Day 30. Network Services and Applications
CompTIA Network+ N10-006 Exam Topics
- 1.2 Compare and contrast the use of networking services and applications
- 1.3 Install and configure the following networking services/applications
Key Topics
Today’s review focuses on several important network services and applications, including VPNs, AAA, DHCP, DNS, and NAT.
VPN
Virtual private networks (VPNs) support secure communication between two sites over an untrusted network, typically the Internet. VPNs are an important tool for remote or telecommuting users to securely access corporate headquarters. VPNs provide a low-cost, efficient method for branch locations to securely connect to corporate headquarters.
Types
The two primary types of VPNs are site-to-site and client-to-site VPNs:
- Site-to-site VPNs provide a low-cost, efficient method for branch locations to securely connect to corporate headquarters. Site-to-site VPNs are usually faster and cost less than leased lines. Figure 30-1 shows an example of a site-to-site VPN.
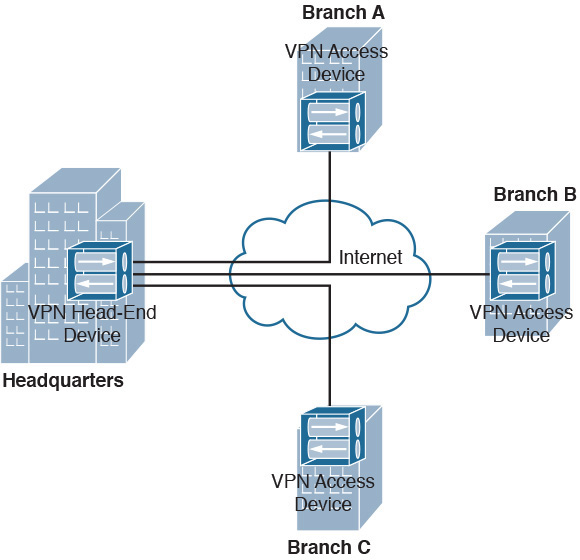
Figure 30-1 Site-to-Site VPN
- Client-to-site VPNs (or remote-access VPNs) are an important tool for remote or telecommuting users to securely access corporate headquarters. Client-to-site VPNs are faster and cost less than traditional dial-up or ISDN connections. Figure 30-2 shows an example of a client-to-site VPN.
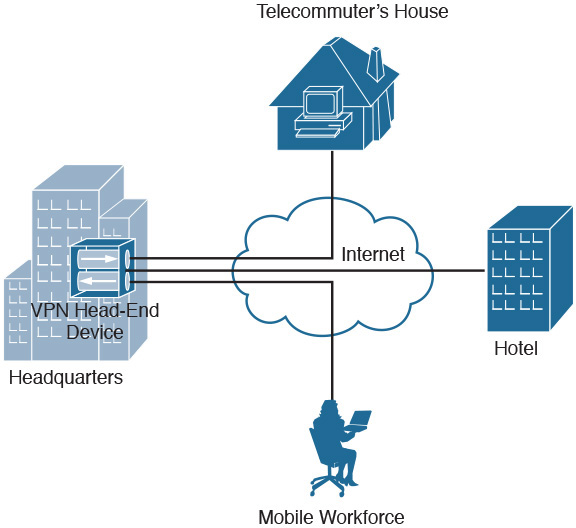
Figure 30-2 Client-to-Site VPN
IPsec and IKE
Internet Protocol Security (IPsec) is a suite of protocols used to create a VPN. IPsec is composed of two separate protocols. Authentication Header (AH) provides the authentication and integrity checking for data packets, and Encapsulating Security Payload (ESP) provides encryption services.
IPsec provides three key security services:
- Data confidentiality ensures that the data sent between the two parties is unreadable by a third party.
- Data integrity ensures that data is not modified in transit.
- Authentication verifies that the party on the other side of the tunnel is the party they claim to be.
Internet Key Exchange (IKE) is the key negotiation and management protocol that is most commonly used to provide dynamically negotiated and updated keying material for IPsec. Specifically, IPsec can use IKE to provide encryption between authenticated peers.
The process of establishing, maintaining, and tearing down an IPsec site-to-site VPN uses IKE and consists of five primary steps, as shown in Figure 30-3:
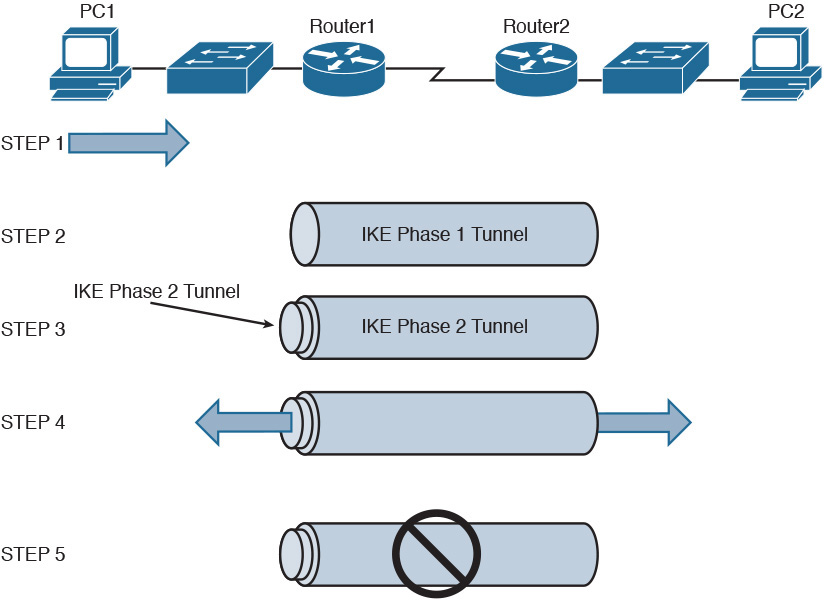
Figure 30-3 Site-to-site IPsec VPN Steps
Step 1. PC1 sends traffic destined for PC2. Router1 classifies the traffic as “interesting” traffic (usually classified as interesting by an ACL), which initiates the creation of an IPsec tunnel.
Step 2. Router1 and Router2 negotiate a security association (SA) used to form an IKE Phase 1 tunnel, which is also known as an Internet Security Association and Key Management Protocol (ISAKMP) tunnel.
Step 3. Within the protection of the IKE Phase 1 tunnel, an IKE Phase 2 tunnel is negotiated and set up. An IKE Phase 2 tunnel is also known as an IPsec tunnel.
Step 4. After the IPsec tunnel is established, interesting traffic flows through the protected IPsec tunnel. Note that traffic not deemed interesting can still be sent between PC1 and PC2. However, the non-interesting traffic is neither authenticated nor encrypted.
Step 5. After no interesting traffic is seen for a specified amount of time, the IPsec tunnel is torn down and the IPsec SA is deleted.
 Activity: Order the Steps for Site-to-Site VPNs
Activity: Order the Steps for Site-to-Site VPNs
Other VPN Technologies
Although IPsec VPNs are popular for securely interconnecting sites or connecting a remote client to a site, you need to be aware of other VPN protocols for the exam, examples of which are provided in Table 30-1.
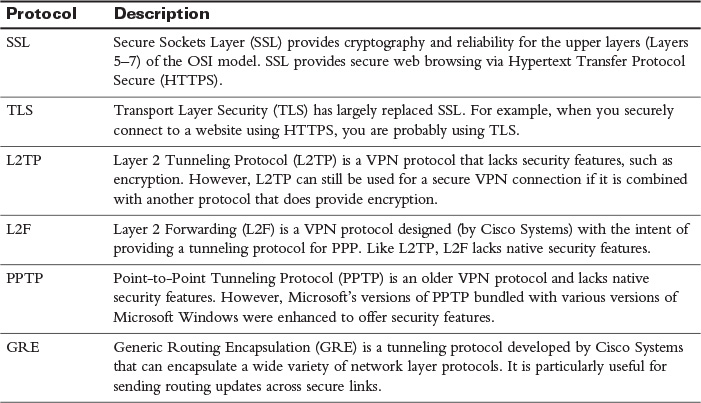
Table 30-1 Examples of VPN Protocols
Remote Access Services
Remote access services include any combination of hardware or software that allows a user to remotely access another device on the network. For the Network+ exam, you need to be able to compare and contrast RADIUS, TACACS+, and Microsoft’s RAS.
AAA Services
Authentication, authorization, and accounting (AAA) services allow an administrator to create and manage one repository for all user credentials. Functionally, AAA works as follows:
- Authentication—Users must prove that they are who they say they are.
- Authorization—Authorization services determine which resources the user can access and which operations the user is allowed to perform.
- Accounting—Accounting keeps track of how network resources are used.
RADIUS and TACACS+ are protocols commonly used to communicate with a AAA server:
- Remote Authentication Dial-In User Service (RADIUS) is a UDP-based protocol used to communicate with a AAA server. Unlike TACACS+, RADIUS does not encrypt an entire authentication packet, but only the password. However, RADIUS does offer more robust accounting features than TACACS+. Also, RADIUS is a standards-based protocol, whereas TACACS+ is a Cisco proprietary protocol.
- Terminal Access Controller Access-Control System Plus (TACACS+) is a TCP-based protocol used to communicate with a AAA server. Unlike RADIUS, TACACS+ encrypts an entire authentication packet, rather than just the password. TACACS+ does offer accounting features, but they are not as robust as the accounting features found in RADIUS. Also, unlike RADIUS, TACACS+ is a Cisco proprietary protocol.
Table 30-2 compares RADIUS and TACACS+.
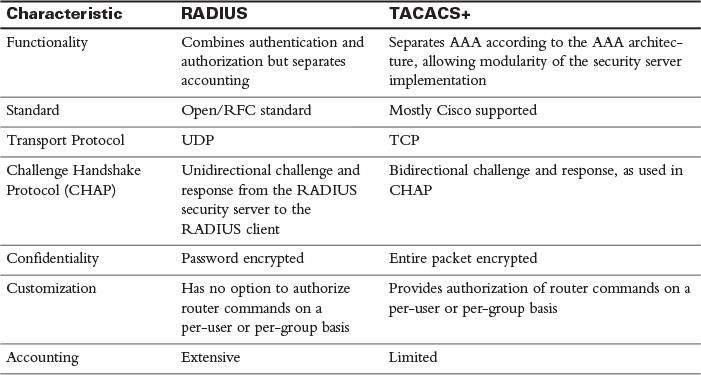
Table 30-2 RADIUS and TACACS+ Comparison
Microsoft’s RAS
Remote access service (RAS) is a remote-access solution included with Windows Server products. Although the system is called RAS, the underlying technologies that enable the RAS process are dial-up protocols such as the Point-to-Point Protocol (PPP). Any system that supports dial-up protocols can connect to a RAS server.
RAS supports remote connectivity from all the major client operating systems available today, including all newer Windows operating systems:
- Windows Server products
- Windows Home–based clients
- Windows Professional–based clients
- Windows Enterprise–based clients
- UNIX-based/Linux clients
- Mac OS X–based clients
Other Remote Access Services
Other remote access services include the following:
- RDP—Remote Desktop Protocol (RDP) is a Microsoft protocol that allows a user to view and control the desktop of a remote computer.
- ICA—Independent Computing Architecture (ICA) is a Citrix Systems proprietary protocol that allows an application running on one platform (for example, Microsoft Windows) to be seen and controlled from a remote client, independent of the client platform (for example, UNIX/Linux).
- SSH—Secure Shell is a protocol used to securely connect to a remote host (typically via a terminal emulator).
- Telnet—Telnet is an unsecure protocol used to connect to a remote host. All traffic, including username and password, is sent in clear text. Telnet should not be used.
Unified Communications
Unified communications (UC), referred to as unified voice services in the Network+ exam topics, combine data, voice, and video all on the same network. UC networks implement Voice over IP (VoIP) to digitize the voice traffic into packets to be transmitted across a data network. Figure 30-4 shows a sample VoIP network topology.
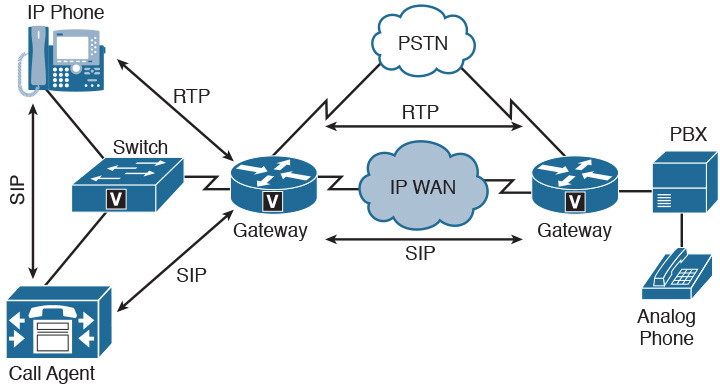
Figure 30-4 VoIP Network Topology
Table 30-3 defines the VoIP devices and protocols shown in Figure 30-4.
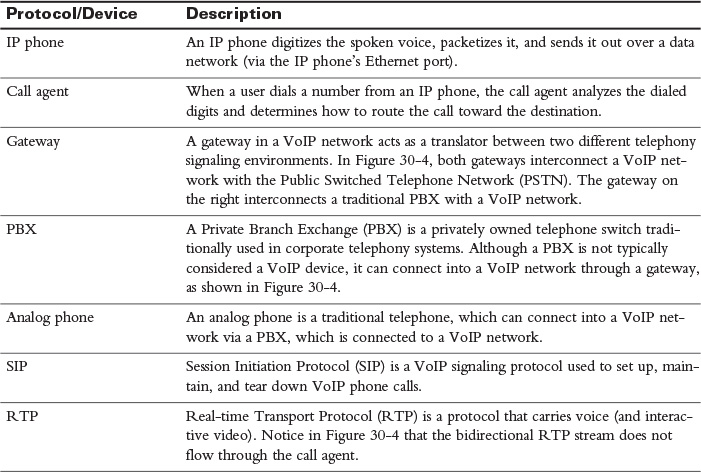
Table 30-3 VoIP Network Elements
DHCP
You could manually assign IP address information to every device on the network. However, static address assignment is time consuming and prone to error. A much more efficient method is to have IP address information assigned dynamically. The most common approach for this auto-assignment of IP addresses is to use Dynamic Host Configuration Protocol (DHCP). Not only does DHCP assign an IP address to a network device, it can assign a wide variety of other IP parameters, such as a subnet mask, a default gateway, and the IP address of a DNS server.
Figure 30-5 illustrates the DHCP process.
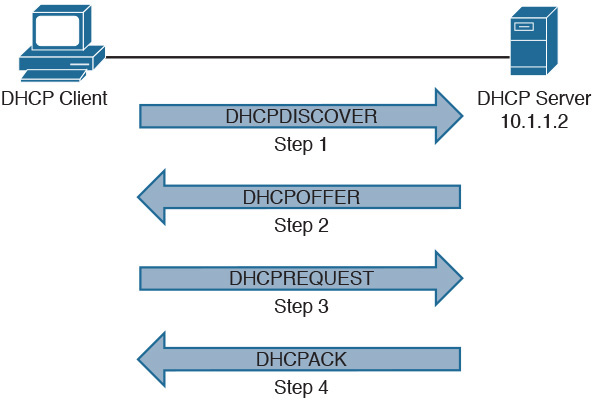
Figure 30-5 DHCP Process
Use the mnemonic DORA to remember the steps in the DHCP process: Discover, Offer, Request, and Acknowledge.
Step 1. DHCPDISCOVER messages are broadcasted by the client when it initially boots to discover DHCP servers.
Step 2. DHCPOFFER messages are replies from DHCP servers.
Step 3. DHCPREQUEST messages are sent by the client request to a particular server’s offer.
Step 4. DHCPACK messages are sent by the DHCP server acknowledging the DHCP client and providing a collection of IP configuration parameters.
DHCP enables ranges of IP addresses, known as scopes, to be defined on a system running a DHCP server application. When another system configured as a DHCP client is initialized, it asks the server for an address. If all things are as they should be, the server assigns an address from the scope to the client for a predetermined amount of time, known as the lease.
At various points during the lease (normally the 50 percent and 85 percent points), the client attempts to renew the lease from the server. If the server cannot perform a renewal, the lease expires at 100 percent, and the client stops using the address.
Some devices on the network, such as servers and printers, may require a consistent IP address. In such cases, the network administrator can configure the DHCP server to reserve specific IP addresses for these clients.
DHCP servers can also be configured to provide clients with other parameters such as DNS servers, domain names, and WINS servers.
If there are no DHCP servers on the same LAN as the client, then the gateway router must be configured to relay DHCP requests to a DHCP server. This is because DHCPDISCOVER messages are broadcasted. By default, broadcast messages are not forwarded by routers.
 Activity: Order the Steps in the DHCPv4 Operation
Activity: Order the Steps in the DHCPv4 Operation
DNS
A Domain Name System (DNS) server performs the task of resolving a domain name to an IP address. As shown in Figure 30-6, an end user who wants to navigate to the www.ciscopress.com website enters that fully qualified domain name (FQDN) into the web browser. The end user’s computer sends a DNS request to the DNS server asking for the IP address that corresponds to www.ciscopress.com. The DNS server responds with 192.168.1.11, and now the end user’s computer can send packets to the destination.
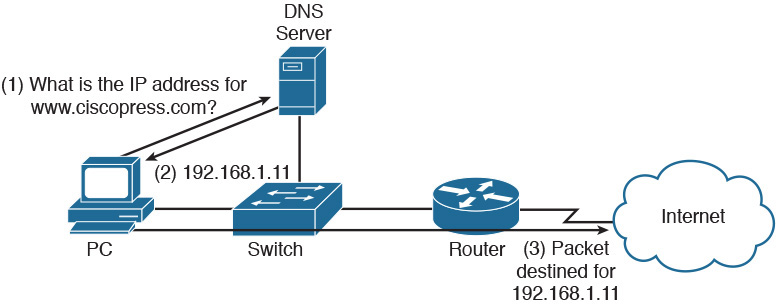
Figure 30-6 DNS Operation
A DNS server maintains a database of local FQDNs and their corresponding IP addresses, in addition to pointers to other servers that can resolve IP addresses for other domains. DNS servers are arranged in a hierarchy, as shown in Figure 30-7.
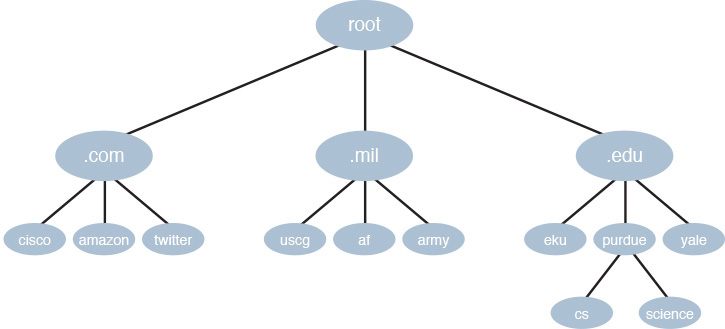
Figure 30-7 DNS Hierarchy
In addition to FQDNs, a DNS server contains other common DNS record types, as shown in Table 30-4.
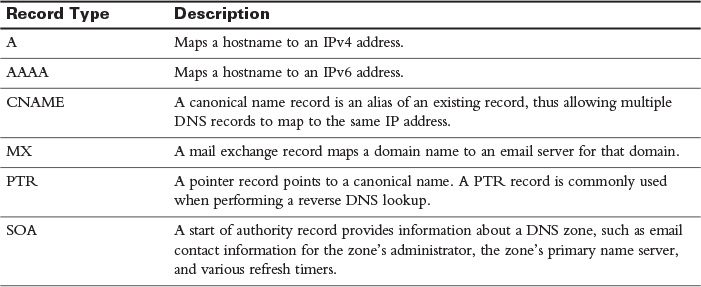
Table 30-4 Common DNS Record Types
What happens if the IP address used by a server changes dynamically? In such a situation, the DNS records would need to be updated. Dynamic DNS providers supply software that monitors the IP address changes and reports any change to the DNS servers.
NAT
Private IPv4 addresses within an organization’s network must be translated to a public IPv4 address before packets can be sent to the public Internet. Network Address Translation (NAT) provides this service. Figure 30-8 summarizes basic NAT operation.
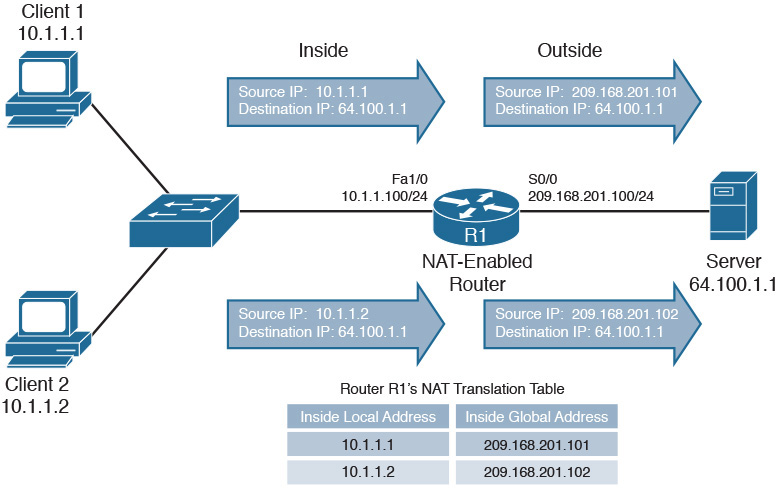
Figure 30-8 NAT Operation
In Figure 30-8, packets from the two client PCs are translated at the NAT-enabled router, R1. The inside local addresses are translated to inside global addresses. Table 30-5 reviews the terminology used when describing the various IP addresses involved in a translation.
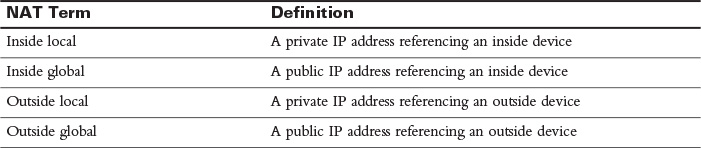
Table 30-5 NAT Terminology
Note
Dynamic NAT should not be confused with destination NAT (DNAT). DNAT, more commonly referred to as port forwarding, is used to change the destination IP address on a packet. Typically, the packet is coming from an outside network, such as the Internet, and is destined for an inside device, such as a server or gaming console.
Sometimes, you want to statically configure the inside global address assigned to a specific device inside your network, such as a web server or email server. This approach to NAT is referred to as Static NAT (SNAT).
The addresses in Figure 30-8 were dynamically assigned to the clients from a pool of available addresses. This is called dynamic NAT. However, this one-to-one dynamic mapping of one private IP address to one public IP address is far less common than another variety of NAT called Port Address Translation (PAT).
PAT allows multiple inside local addresses to share a single inside global address. PAT does this by tracking source and destination port numbers as well as the inside local and inside global addresses. Figure 30-9 summarizes PAT operation.
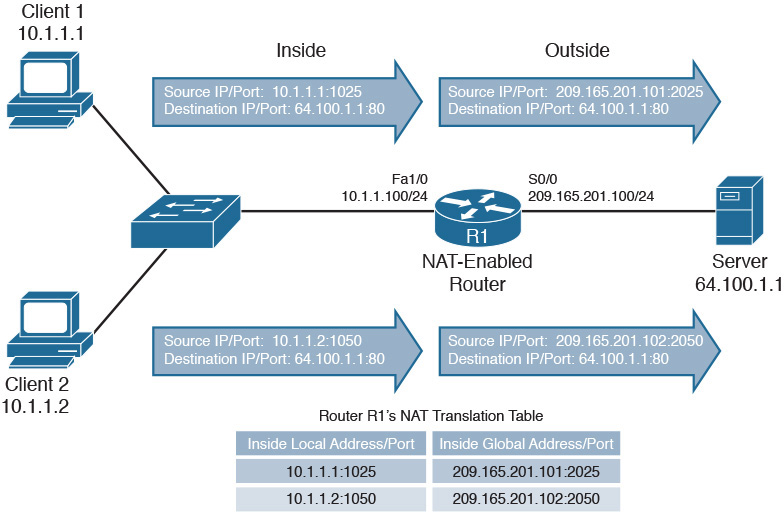
Figure 30-9 PAT Operation
 Video 30.1—NAT - Network Address Translation
Video 30.1—NAT - Network Address Translation
 Video 30.2—Exploring NAT Translation from the Network Client/Host
Video 30.2—Exploring NAT Translation from the Network Client/Host
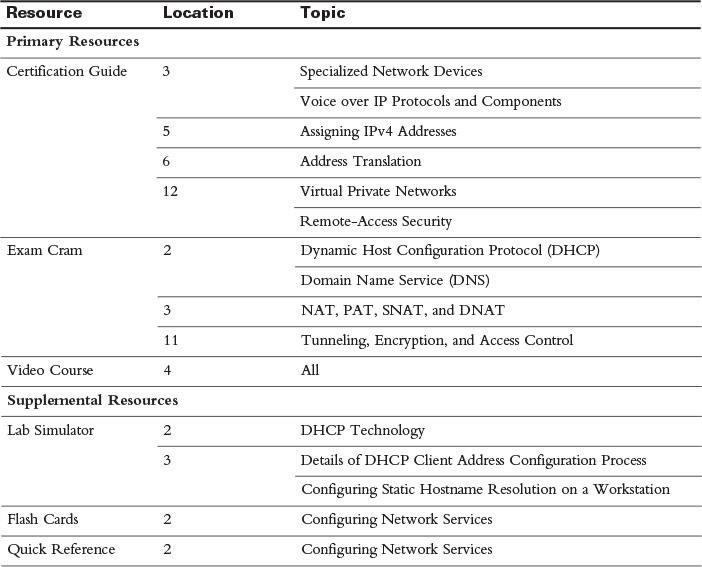
Study Resources
For today’s exam topics, refer to the following resources for more study.
 Check Your Understanding
Check Your Understanding