Day 29. Cryptographic Technologies
CCNA Security 210-260 IINS Exam Topics
- 1.3.a Describe key exchange
- 1.3.b Describe hash algorithm
- 1.3.c Compare and contrast symmetric and asymmetric encryption
- 1.3.d Describe digital signatures, certificates, and PKI
Key Topics
Today we will review cryptographic technologies and terminology. In particular, we will look at understanding the challenges of secure key management within a network environment. As well, we will review the different types of hashing algorithms in use today for data integrity. We will compare and contrast symmetric and asymmetric encryption algorithms, and finally delve into digital signatures and certificates. We will review PKI tomorrow.
CIA Triad
Before looking at the different cryptographic technologies in use today, it is important to understand the basic premise of cryptography itself. Cryptography is the practice and study of techniques to secure communications in the presence of third parties. Historically, cryptography was synonymous with encryption. Its goal was to keep messages private. Today, cryptography includes other responsibilities:
- Confidentiality: Uses encryption algorithms to encrypt and hide data
- Data integrity: Uses hashing algorithms to ensure that data is unaltered during any operation
- Authentication: Ensures that any messages received were actually sent from the perceived origin
Key Exchange and Management
Key management deals with the secure generation, verification, exchange, storage, and destruction of keys. It is extremely important to have secure methods of key management. Key exchange and management are often considered the most difficult part of designing a cryptosystem. Many cryptosystems have failed because of mistakes in their key management, and all modern cryptographic algorithms require key management procedures. The basic components of any key management system include (1) automated and randomized key generation, (2) key strength verification, (3) encrypted key storage, (4) secure key exchange, (5) short key lifetimes, and (6) revocation and destruction of compromised or expired keys.
Hash Algorithms
Hashing is a mechanism that is used for data integrity assurance. Hashing is based on a one-way mathematical function that is relatively easy to compute but significantly difficult to reverse. Figure 29-1 illustrates how hashing is performed. Data of an arbitrary length is input into the hash function, and the result of the hash function is the fixed-length hash, which is known as the “digest” or “fingerprint.”
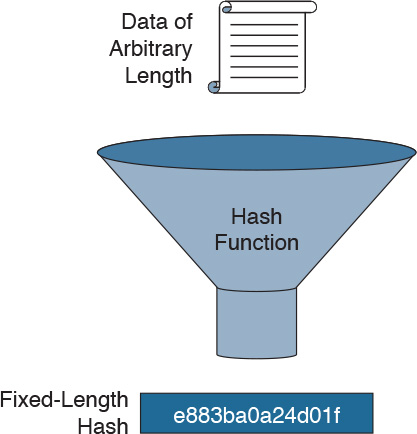
Figure 29-1 Hash Function
Well-known Hash Functions
Hash functions are helpful when ensuring data is not changed accidentally, such as by a communication error. Although hashing can be used to detect accidental changes, it cannot be used to guard against deliberate changes. There is no unique identifying information from the sender in the hashing procedure. Therefore, hashing is vulnerable to man-in-the-middle attacks and does not provide security to transmitted data.
The following are the three most commonly used cryptographic hash functions:
- Message Digest 5 (MD5): MD5 is a one-way function that makes it easy to compute a hash from the given input data but makes it very difficult to compute input data given only a hash value. MD5 produces a 128-bit hash and is now considered a legacy algorithm that should be avoided.
- Secure Hash Algorithm 1 (SHA-1): SHA-1 takes a message of up to 2^64 bits in length and produces a 160-bit message digest. The algorithm is slightly slower than MD5, but the larger message digest makes it more secure against brute-force collision and inversion attacks. It is now considered legacy and should be avoided when possible.
- Secure Hash Algorithm 2 (SHA-2): SHA-2 algorithms are the secure hash algorithms that the U.S. government requires by law for use in certain applications. The SHA-2 family includes 224-bit, 256-bit, 384-bit, and 512-bit functions. When choosing a hashing algorithm, use SHA-256 or higher, as they are currently the most secure.
Caution
Security flaws were discovered in SHA-1 and MD5. Therefore, it is now recommended that these algorithms be avoided.
Authentication Using Hashing
Two systems that have agreed on a secret key can use the key along with a hash function to verify data integrity of communication between them by using a keyed hash. A message authentication code is produced by passing the message data along with the secret key through a hash algorithm. Only the sender and the receiver know the secret key, and the output of the hash function now depends on the message data and the secret key. Figure 29-2 illustrates how the message authentication code is created. Data of an arbitrary length is input into the hash function, together with a secret key. The result is the fixed-length hash that depends on the data and the secret key. This type of authentication is referred to as keyed-hash message authentication code (HMAC) and adds authentication to integrity assurance.
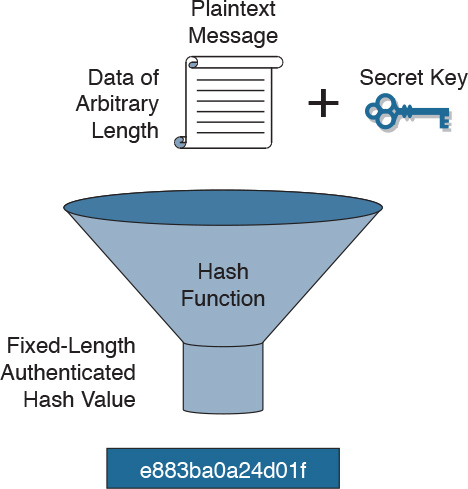
Figure 29-2 HMAC Hashing
HMAC functions can be used with MD5 (HMAC-MD5) or SHA-1 (HMAC-SHA-1). Figure 29-3 illustrates cryptographic authentication in action. The sender, Alice, wants to ensure that the message is not altered in transit and wants to provide a way for the receiver, Bob, to authenticate the origin of the message.
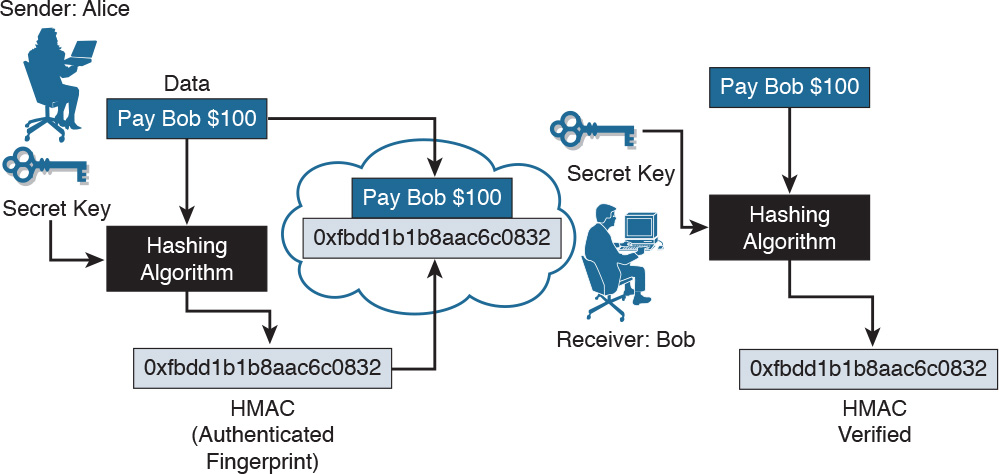
Figure 29-3 HMAC in Action
Alice inputs data and the secret key into the hashing algorithm and calculates the fixed-length message authentication code, or fingerprint. This authenticated fingerprint is then attached to the message and sent to Bob. Bob removes the fingerprint from the message and uses the received message with his copy of the secret key as input to the same hashing function. If the fingerprint that is calculated is identical to the fingerprint that was received, then data integrity has been verified. Also, the origin of the message is authenticated, because only Alice possesses a copy of the shared secret key.
Hashing in Cisco Products
Cisco products use hashing for entity authentication, data integrity, and data authenticity purposes such as
- IPsec gateways and clients use hashing algorithms to verify packet integrity and authenticity.
- Cisco IOS routers use keyed hashing with secret keys to add authentication information to routing protocol updates.
- Cisco software images that you can download from Cisco.com have MD5 and SHA-512 based checksums available, so that customers can check the integrity of downloaded images.
Symmetric and Asymmetric Encryption
Before diving into the differences between symmetric and asymmetric encryption algorithms, let’s first start by reviewing the basic concepts of encryption itself.
Encryption Overview
Encryption is the process of disguising a message in such a way as to hide its original contents. With encryption, the plaintext readable message is converted to ciphertext, which is the unreadable, “disguised” message. Decryption reverses this process. Encryption is used to guarantee confidentiality so that only authorized entities can read the original message.
Encryption can provide confidentiality at different network layers, such as the following:
- Encrypting application layer data, such as encrypting email messages with Pretty Good Privacy (PGP)
- Encrypting session layer data using a protocol such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS)
- Encrypting network layer data using protocols such as those provided in the IP security (IPsec) protocol suite
- Encrypting data link layer data using proprietary link-encrypting devices
A good cryptographic algorithm is designed in such a way that it resists common cryptographic attacks. Variable key lengths and scalability are also desirable attributes of a good encryption algorithm. A key is a required parameter for encryption algorithms to encrypt and decrypt a message. The key is the link between the plaintext and ciphertext. There are two classes of encryption algorithms, which differ in their use of keys:
- Symmetric encryption algorithms: Use the same key to encrypt and decrypt data
- Asymmetric encryption algorithms: Use different keys to encrypt and decrypt data
Symmetric Encryption Algorithms
Symmetric, or secret key, encryption is the most commonly used form of cryptography because the shorter key length increases the speed of execution. The typical key-length range of symmetric encryption algorithms is 40 to 256 bits. Figure 29-4 illustrates an example of symmetric encryption in action.
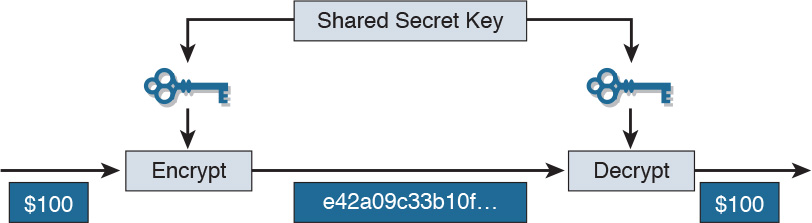
Figure 29-4 Symmetric Encryption Example
In this example, the same key is used to encrypt the data by the sender and decrypt the data by the recipient.
With symmetric encryption, key management can be a challenge. The encryption and decryption keys are the same. The sender and the receiver must exchange the symmetric, secret key using a secure channel before any encryption can occur.
Table 29-1 provides a summary of the types of symmetric encryption algorithms in use today and their respective key lengths.
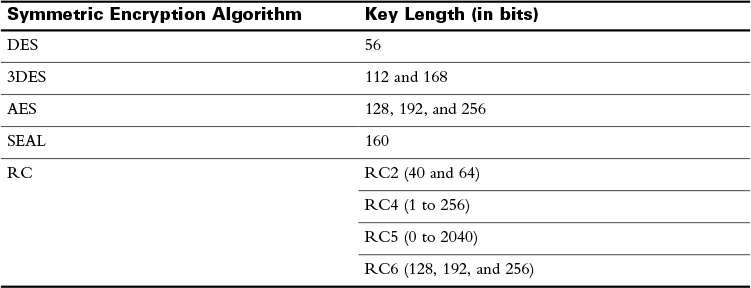
Table 29-1 Symmetric Encryption Algorithms
DES is considered a legacy algorithm and is vulnerable to brute-force attacks. One way to increase the effectiveness of DES, without changing the well-analyzed algorithm itself, is to use the same algorithm with different keys several times in a row. The technique of applying DES three times in a row to a plaintext block is called 3DES. Brute-force attacks on 3DES are considered unfeasible today. Because the basic algorithm has been well tested in the field for more than 35 years, it is considered very trustworthy. For several years, it was recognized that DES would eventually reach the end of its usefulness. In 1997, the AES initiative was announced. AES was chosen to replace DES and 3DES, because the key length of AES is much stronger than that of DES, and AES runs faster than 3DES on comparable hardware.
 Video 29.1—Symmetric Encryption
Video 29.1—Symmetric Encryption
Asymmetric Encryption Algorithms
Asymmetric encryption algorithms use a pair of keys to encrypt and decrypt data. Secure messages can be exchanged without having to have a pre-shared key. Because neither party has a shared secret, very long key lengths must be used. These algorithms are resource intensive and slower to execute. Most commonly, an entity with a key pair will share one of the keys (the public key) and keep the other key in complete secrecy (the private key). The private key cannot, in any reasonable amount of time, be calculated from the public key. Data that is encrypted with the private key requires the public key to decrypt. Vice versa, data that is encrypted with the public key requires the private key to decrypt. Asymmetric encryption is also known as public key encryption.
Here is one possible scenario of asymmetric encryption in action. In Figure 29-5, imagine that Bob has generated a public/private key pair. Bob keeps the private key totally secret but publishes the public key so it is available to everyone. Alice has a message that she wants to send to Bob in private. If Alice encrypts the message using Bob’s public key, only Bob has the private key that is required to decrypt the message, providing confidentiality.
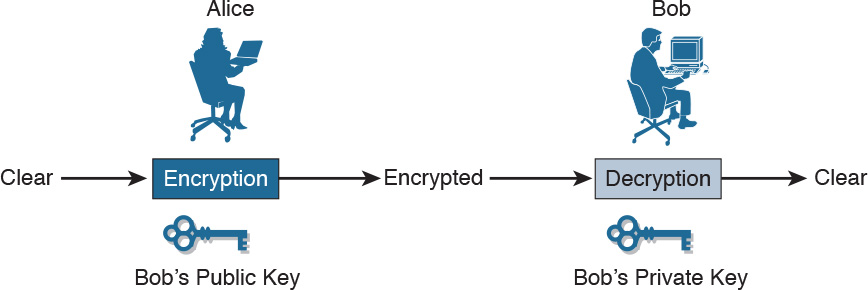
Figure 29-5 Asymmetric Encryption Example
The following table provides a detailed comparison between symmetric and asymmetric encryption algorithms:
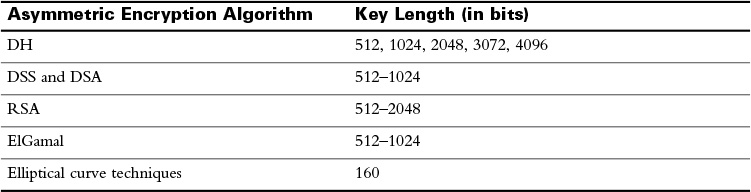
Four protocols that use asymmetric encryption algorithms are
- Internet Key Exchange (IKE): A fundamental component of IPsec VPNs
- Secure Sockets Layer (SSL): Now implemented as IETF standard TLS
- Secure Shell (SSH): Provides a secure remote-access connection to network devices
- Pretty Good Privacy (PGP): A computer program that provides cryptographic privacy and authentication
 Video 29.2—Asymmetric Encryption
Video 29.2—Asymmetric Encryption
 Video 29.3—Comparing Symmetric and Asymmetric Encryption Algorithms
Video 29.3—Comparing Symmetric and Asymmetric Encryption Algorithms
 Activity: Compare Symmetric and Asymmetric Encryption Algorithms
Activity: Compare Symmetric and Asymmetric Encryption Algorithms
Digital Signatures and RSA Certificates
Digital signatures provide the same functionality as handwritten signatures. Specifically, they are a mathematical technique used to provide three basic security services: authenticates a source, proving that a certain party has seen and signed the data in question; guarantees that the data has not changed from the time it was signed; proves to a third party that the data exchange did take place.
Digital signatures are commonly used in code signing (to verify the integrity of downloaded files) and digital certificates (to verify the identity of an organization or individual). The basic four properties of digital signatures are that (1) the signature is authentic, (2) the signature is not forgeable, (3) the signature is not reusable, and (4) the signer cannot claim later that they did not sign it.
Digital certificates are used to authenticate and verify that a user sending a message is who they claim to be. Figure 29-6 shows how an RSA digital certificate or signature is used. RSA is an asymmetric algorithm that is commonly used for generating and verifying digital signatures. In this scenario, Bob is confirming an order with Alice. The steps are as follows:
1. Bob makes a hash, or fingerprint, of the document, which uniquely identifies the document and all its contents.
2. Bob encrypts the hash with only the private key of the signer (i.e., Bob’s private key).
3. The encrypted hash, which is known as the signature, is appended to the document.
4. Alice obtains Bob’s public key.
5. Alice decrypts the signature using Bob’s public key. This step reveals the hash value initially calculated by Bob.
6. Alice makes a hash of the received document, without its signature, and compares this hash to the decrypted signature hash sent by Bob. If the hashes match, the document is authentic. The match means that the document has been signed by Bob and has not changed since it was signed.
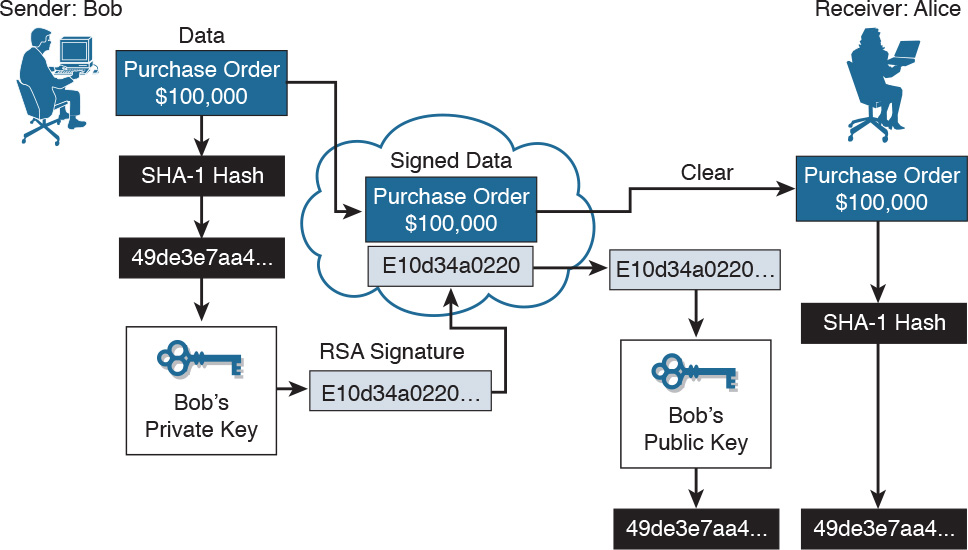
Figure 29-6 Using RSA Digital Signatures
Study Resources
For today’s exam topics, refer to the following resources for more study.
 Check Your Understanding
Check Your Understanding